360º PRIVILEGE PLATFORM
Only solution covers the complete privileged access management lifecycle, providing governance before, during and after privileged access events

Privilege abuse today
Organization’s often demanded control over people’s access.
- With cloud use the need for machine automation became a reality. Managing people's privilege access inside of a company it’s insufficient.
- The complexity and the scale of access management offers a bigger threat to organization’s data sovereignty.
-
Combined with the variety of devices, IoT and DevOps have made privilege abuse a problem of a higher scale.
- It’s time to control privilege access for machines and applications from inside and out of the organization.
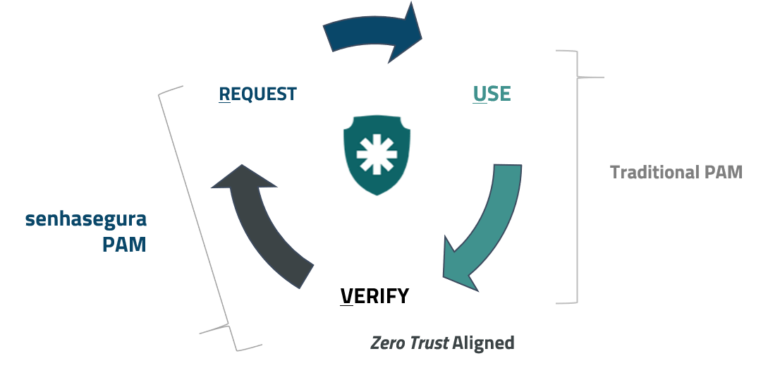
How to stop privilege abuse?
Request, Use, Verify (RUV) Method for continuous Improving security. Manages the entire privileged access lifecycle.
- Request: Identity assurance by access governance and identity management certificates.
- Use: Manage human and machine privileged access, including 3rd party and endpoints.
- Verify: Automatically audit changes in settings made by privileged users after sessions have been finished.
See how senhasegura works
Privileged Access Management (PAM) Flow:
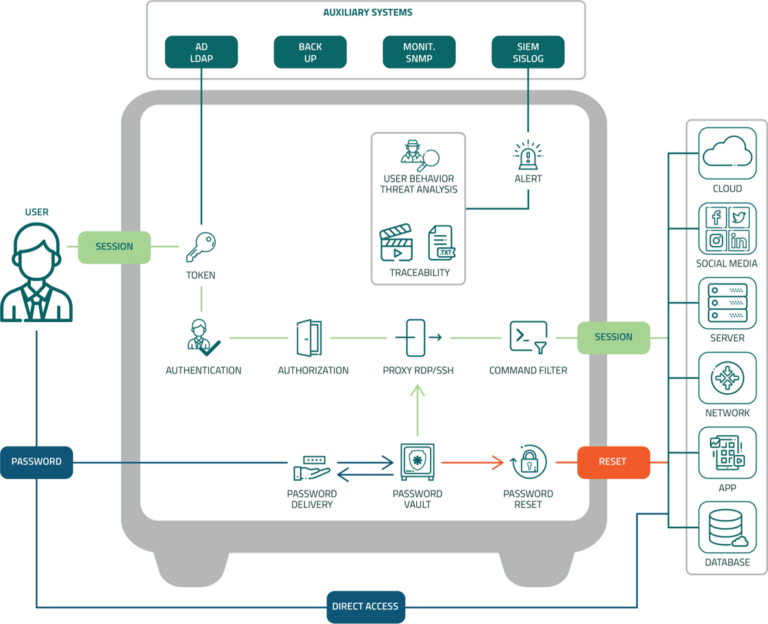
What Senhasegura can do for you

Security and Risk Management

Compliance and Audit

DevOps Secret Management

Cloud Security

Privileged Identity

Privileged Access

Privileged Auditing

Privileged Infrastructure
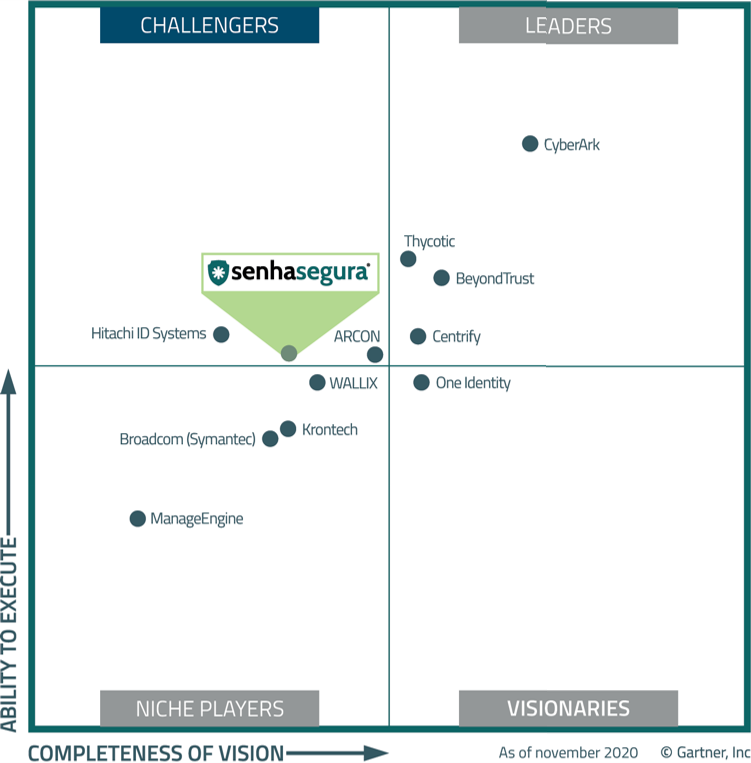
Gartner names senhasegura as Challenger among 10 best global PAM technologies
To guide its customers seeking a good PAM solution, Gartner produces Gartner Magic Quadrant for PAM, listing and ranking the leading solutions on the market.
senhasegura solution had a big jump from the 2018 report to the 2020 report, leaving the Visionaries category and consolidating a Challenger solution.
The 2020 report highlights following main points:
Main PAM solution brand in Latin America.
Very efficient RDP proxy function.
Great performance for session management.
Advanced features on discoveries and account mapping.
A PAM solution that covers the PAM life cycle.